 The importance of ISC2 CISSP Training has never been as crucial as in today's IT Industry. More and more today, companies rely on the network for the storage and fast retrieval of mission-critical corporate data and information. Securing these massive amounts of sensitive data is critical for the success of the organization and one of the main reasons that security has become one of the most important areas of IT specialization available. The importance of ISC2 CISSP Training has never been as crucial as in today's IT Industry. More and more today, companies rely on the network for the storage and fast retrieval of mission-critical corporate data and information. Securing these massive amounts of sensitive data is critical for the success of the organization and one of the main reasons that security has become one of the most important areas of IT specialization available.
As the first ANSI ISO accredited credential in the field of information security, the Certified Information Systems Security Professional CISSP certification provides information security a globally recognized standard of achievement. Considered the gold standard in the information security realm, this credential gives prospective employers an invaluable tool in validating candidates' expertise in securing an enterprise, and provides global recognition for top information security professionals.
Our CISSP Computer Security Training Course is designed to cover all ten domains as well as prepare you for the ISC2 certification exam. We offer online 24 x 7 instructor mentoring to answer any of your questions day or night. Our Printable transcripts makes reviewing subject matter a breeze.
Training Course Includes
 Full Multi Media Training Courses Full Multi Media Training Courses
Test Preps- Hundreds of practice exams online
Certificate of Completion
One Year of Free Upgrades of training course
Training Time 30 Hours
We also offer
CISSP 7 Day Live Boot Camp
CISSP Training Course Description
Training Prerequisites
A minimum of five years of direct full-time security professional work experience in two or more of the 10 domains of the (ISC)² CISSP CBK is recommended.
This course prepares learners for the examination requirement of this valuable certification, focusing on the 10 domains covered by the Common Body of Knowledge (CBK), as outlined by the ISC2 organization:
Course Outline
- Access Control
- Telecommunications and Network Security
- Information Security Governance and Risk Management
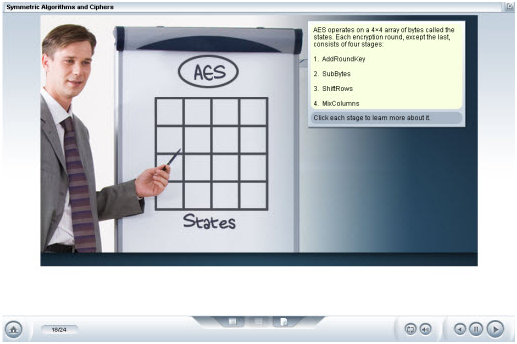
- Cryptography
- Operations Security
- Business Continuity and Disaster Recovery Planning
- Legal, Regulations, Investigations, and Compliance
- Physical (Environment) Security
- Security Architecture and Design
- Software Development Security
|